[fun] Linus and SHA1


From the Crypto ‘88 conference, 1988
A specter is haunting the modern world, the specter of crypto anarchy.
Computer technology is on the verge of providing the ability for individuals and groups to communicate and interact with each other in a totally anonymous manner. Two persons may exchange messages, conduct business, and negotiate electronic contracts without ever knowing the True Name, or legal identity, of the other. Interactions over networks will be untraceable, via extensive re-routing of encrypted packets and tamper-proof boxes which implement cryptographic protocols with nearly perfect assurance against any tampering. Reputations will be of central importance, far more important in dealings than even the credit ratings of today. These developments will alter completely the nature of government regulation, the ability to tax and control economic interactions, the ability to keep information secret, and will even alter the nature of trust and reputation.
The technology for this revolution–and it surely will be both a social and economic revolution–has existed in theory for the past decade. The methods are based upon public-key encryption, zero-knowledge interactive proof systems, and various software protocols for interaction, authentication, and verification. The focus has until now been on academic conferences in Europe and the U.S., conferences monitored closely by the National Security Agency. But only recently have computer networks and personal computers attained sufficient speed to make the ideas practically realizable. And the next ten years will bring enough additional speed to make the ideas economically feasible and essentially unstoppable. High-speed networks, ISDN, tamper-proof boxes, smart cards, satellites, Ku-band transmitters, multi-MIPS personal computers, and encryption chips now under development will be some of the enabling technologies.
The State will of course try to slow or halt the spread of this technology, citing national security concerns, use of the technology by drug dealers and tax evaders, and fears of societal disintegration. Many of these concerns will be valid; crypto anarchy will allow national secrets to be trade freely and will allow illicit and stolen materials to be traded. An anonymous computerized market will even make possible abhorrent markets for assassinations and extortion. Various criminal and foreign elements will be active users of CryptoNet. But this will not halt the spread of crypto anarchy.
Just as the technology of printing altered and reduced the power of medieval guilds and the social power structure, so too will cryptologic methods fundamentally alter the nature of corporations and of government interference in economic transactions. Combined with emerging information markets, crypto anarchy will create a liquid market for any and all material which can be put into words and pictures. And just as a seemingly minor invention like barbed wire made possible the fencing-off of vast ranches and farms, thus altering forever the concepts of land and property rights in the frontier West, so too will the seemingly minor discovery out of an arcane branch of mathematics come to be the wire clippers which dismantle the barbed wire around intellectual property.
Arise, you have nothing to lose but your barbed wire fences!
Timothy C. May -
tcmay@netcom.com
Piece of cake… As root:
bioctl -P $DISK
where $DISK is the target disk.
Para criar um thumbdrive com crypto no OpenBSD.
Primeiro coloque o seu drive no seu pc. Use o dmesg para pegar o id do device que voce acabou de colocar, deve ser as ultimas linhas, logo:
dmesg | tail
No meu caso retornou:
sd2 at scsibus4 targ 1 lun 0: <Kingston, DataTraveler 3.0, PMAP> removable serial.09511666E3A08995038B
sd2: 59148MB, 512 bytes/sector, 121135104 sectors
OK, agora eu sei que o device que coloquei esta’ como sd2. Vamos limpar de fato o nosso device.
dd if=/dev/urandom of=/dev/rsd2c bs=1m
Isso vai escrever por todo device random bytes, limpando o que estiver la’ dentro. Isso pode/vai demorar um pouco.
Depois de zerar nosso device, vamos criar o registro MBR nele.
fdisk -iy sd2
Agora podemos criar uma particao com o formato RAID usando o disklabel.
disklabel -E sd2
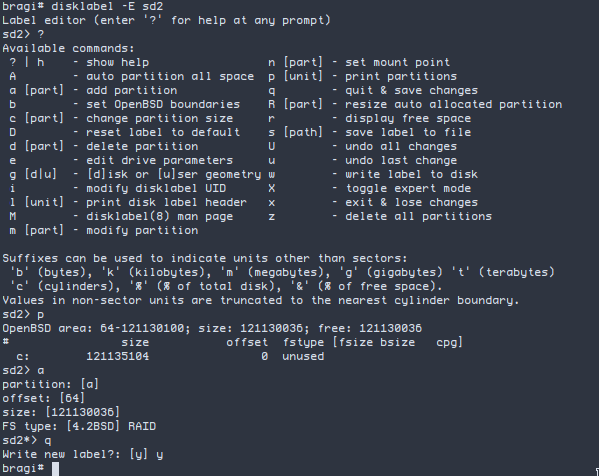
Agora que criamos nossa particao a do tipo RAID. Vamos criar, um device raidsoft0 usando crypto.
bioctl -c C -l sd2a softraid0
Ele vai te perguntar o passphrase que voce deseja usar.
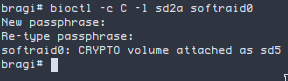
No final do processo ele vai te indicar o device id que foi gerado. No meu caso foi sd5. Agora podemos organizar o device e criar nossa particao e filesystem.
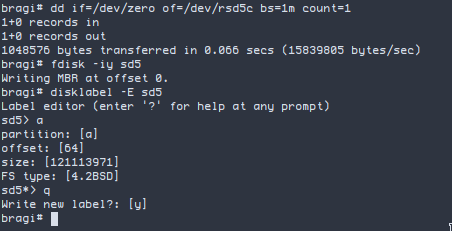
dd if=/dev/zero of=/dev/rsd5c bs=1m count=1
fdisk -iy sd5
disklabel -E sd5
O processo de criacao da particao e’ o mesmo que o anterior, porem agora vamos deixar o FS type padrao.
Por fim, criando o filesystem…
newfs sd5a
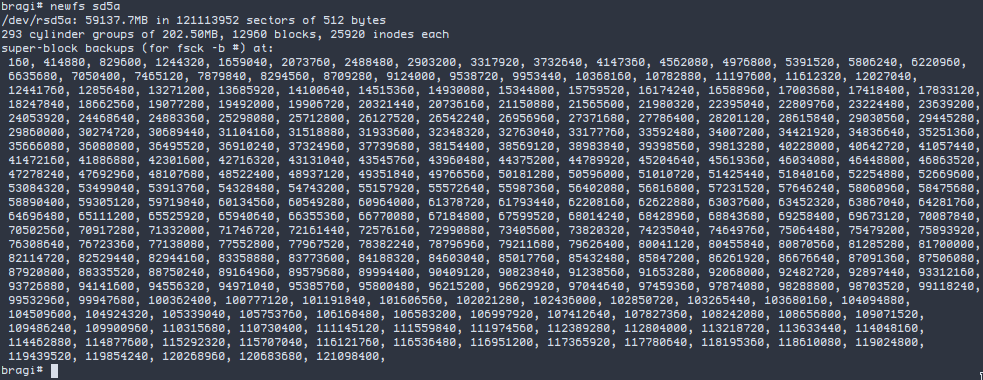
Seu device esta’ pronto para mount e uso.
Lembre-se de utilizar o bioctl depois de usar seu device.
bioctl -d sd5
age e’ uma ferramenta simples, moderna e segura para cryptografar seus arquivos.
Ele usa chaves privadas e publicas para encryptar arquivos. Voce pode gerar uma chave “age” mesmo, ou usar a sua chave ssh1.
No nosso querido OpenBSD…
pkg_add age
Para encryptar um arquivo…
age -e -R ~/.ssh/id_ed25519.pub -o target-file input-file
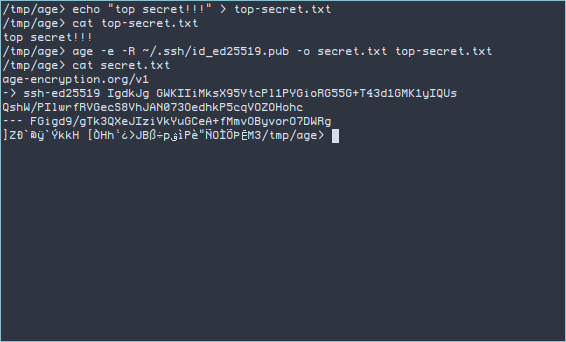
Aqui voce pode ver que o conteudo do arquivo gerado (secret.txt) esta’ cryptografado.
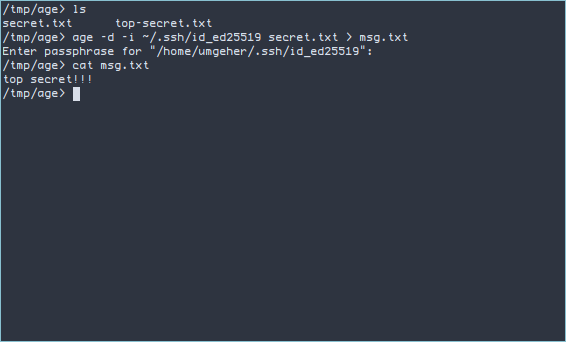
Para descryptar usando a sua chave privada…
age -d -i ~/.ssh/id_ed25519 input-file > output-file
/comments ~umgeher/changelog@lists.sr.ht?Subject=Re: [fun] Linus and SHA1
/permalink https://umgeher.org/posts/2023/03/fun-linus-and-sha1.html